Skip to main contentOverview
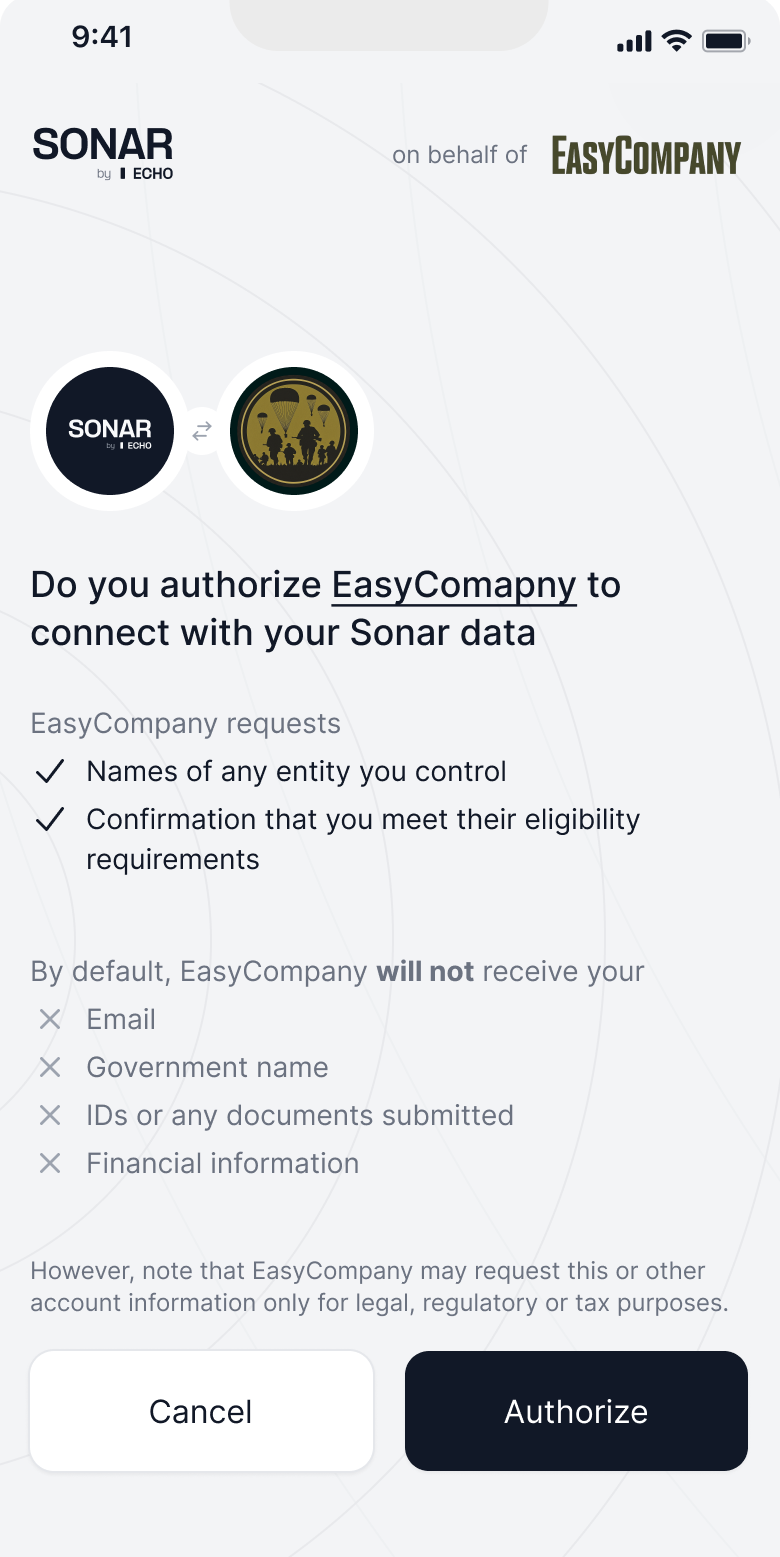
Sonar uses OAuth 2.0 with PKCE for secure authentication. Users sign in through Echo’s OAuth flow to access their compliance entities and generate purchase permits.
How It Works
- User clicks “Sign in with Sonar”
- Redirected to Echo for authentication
- User signs in or creates account
- User authorizes your application to access their data
- Redirected back to your app with auth code
- Your app exchanges code for access token
- Token used for API calls (entities, permits, etc.)
Authentication Configuration
Your OAuth configuration is done through the Founder dashboard. You must configure the following:
- Redirect URIs: A list of URIs that are valid for Sonar to redirect to after the authorization process.
- Scopes: A list of scopes that the client can request from the user.
- Branding: Upload logos and customize the OAuth experience.
Redirect URIs
When setting up your client, you can add one or more redirect URIs. These are the URIs that Sonar will redirect to after the authorization process.
For local development, you must add the following redirect URI to your client, e.g.:
http://localhost:3000/oauth/callback
Scopes
When setting up your client, you can choose which scopes are required for you app, and which are optional.
The following scopes are available:
read_entities: Read entity information and eligibility status.sale_eligibility_check: Check eligibility for sales.contact_email: Access user’s contact email.
To run a sale, you must have the read_entities and sale_eligibility_check scopes, so these should be required. You can choose to add other scopes as either optional or required. For example, if you want to allow the user to share their email with you, you can add the contact_email scope as optional. If you want to require the user to share their email with you, you would add it as required.
Branding
You must supply two logos for the OAuth screen: one for the square logo, and one for the wide logo.
An example of how the OAuth screen will look is shown below: